Cisco Talos Intelligence recently published a comprehensive report on the tactics, techniques, and procedures of 14 prominent ransomware groups active between 2023 and 2024. The report offers vital insights into existing ransomware strategies and recommendations for risk mitigation.
Initial Access: Ransomware groups typically gain access to target systems via phishing or exploiting known vulnerabilities, especially in public-facing applications. This is often followed by lateral movement techniques to extend their reach within the network.
Defense Evasion: Attackers disable or modify security software, obfuscate code, and use legitimate tools such as PowerShell and Windows Management Instrumentation to blend in with regular network traffic. This makes it challenging for security solutions to differentiate between malicious and legitimate activities.
Credential Access: Attackers frequently target Local Security Authority Subsystem Service (LSASS) memory to extract credentials, allowing lateral movement to access critical systems without detection.
Command and Control: Legitimate remote monitoring and management tools enable attackers to control compromised systems while avoiding detection. Since such tools are often allowed in organizations, it is easier for ransomware attackers to operate undetected.
The report identified several notable ransomware groups:
AlphV/Blackcat and Rhysida: Known for their wide range of TTPs, these groups are very adaptive, often customizing their attacks to their target environment.
BlackBasta and LockBit: These attackers are notorious for their aggressive tactics, focusing on encrypting data and disrupting systems to maximize pressure on victims to pay the ransom.
Clop: This group primarily engages in data theft and extortion without always encrypting the victims’ data. They focus on exfiltrating sensitive information and threatening to release it publicly if the ransom is unpaid.
Ransomware groups often focus on a few high-impact unpatched vulnerabilities:
CVE-2018-13379: This flaw targets Fortinet’s SSL VPN, allowing attackers to gain unauthorized access to networks by exploiting a path traversal flaw.
CVE-2020-1472 (Zerologon): This vulnerability allows privilege escalation within domain controllers, making it a prime target for attackers aiming to control an entire network.
CVE-2023-0669: This vulnerability affects the GoAnywhere MFT software, enabling arbitrary code execution, which attackers can use to take over affected systems.
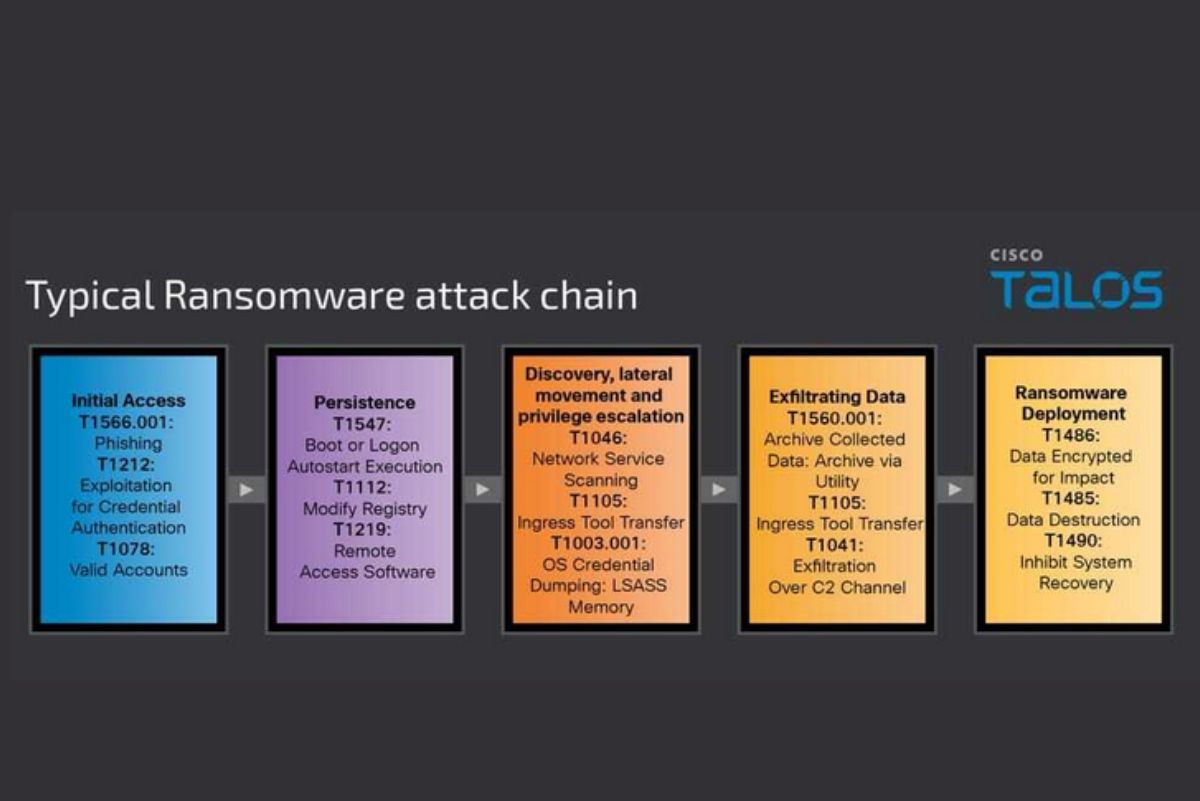
A typical ransomware attack chain involves several stages:
Initial Access: Gained through malicious attachments, phishing emails, or vulnerabilities in public-facing applications.
Execution: Malicious payloads are executed on the victim’s machine, often through scripts or malicious documents.
Persistence: The attacker establishes persistence by adding registry entries, setting up scheduled tasks, or using legitimate tools.
Privilege Escalation: Attackers escalate their privileges to gain higher-level access within the network.
Credential Access: Techniques like credential dumping from LSASS memory are used to obtain authentication details.
Lateral Movement: Attackers move laterally across the network to identify and access critical systems.
Data Exfiltration: Sensitive data is exfiltrated before the encryption process begins.
Impact: Ransomware is deployed to encrypt data and render systems inoperable until the ransom is paid.
The report also outlines important best practices to help organizations minimize the risk of ransomware attacks:
Patch Management: Regularly update systems to fix vulnerabilities, focusing on high-impact flaws frequently targeted by attackers.
Password Policies and MFA: Enforce strong passwords and multi-factor authentication (MFA) measures to reduce the risk of unauthorized access and credential theft.
System Hardening: Disable unnecessary services and apply security configurations to reduce the overall attack surface.
Network Segmentation: Isolate sensitive data and systems to minimize lateral movement and limit the impact of a potential breach.
Continuous Monitoring: Implement Endpoint Detection and Response (EDR/XDR) and Security Information and Event Management (SIEM) solutions to detect and respond to suspicious activities in real-time.
Limit Privilege: Restrict user access to essential functions, minimizing potential damage from compromised accounts.
Reduce IT Exposure: Minimize the number of public-facing services to reduce potential entry points.
The Cisco Talos report highlights the growing sophistication of modern ransomware groups and the need for stringent security measures. By implementing the recommended mitigation strategies, organizations can better defend against such threats and ensure the security of their systems and data.