Reports
New Report Highlights the Rising Threat and Scale of DDoS Attacks
Distributed Denial of Service (DDoS) attacks are escalating at an unprecedented pace, posing a sever...

Distributed Denial of Service (DDoS) attacks are escalating at an unprecedented pace, posing a sever...

The Central Bureau of Investigation (CBI) probed a series of complex cyber crimes in 2023, with sign...

The Centers for Medicare & Medicaid Services (CMS) announced earlier this month that a data brea...

The Reserve Bank of India's (RBI) Currency and Finance report for 2023-24 reveals that the avera...
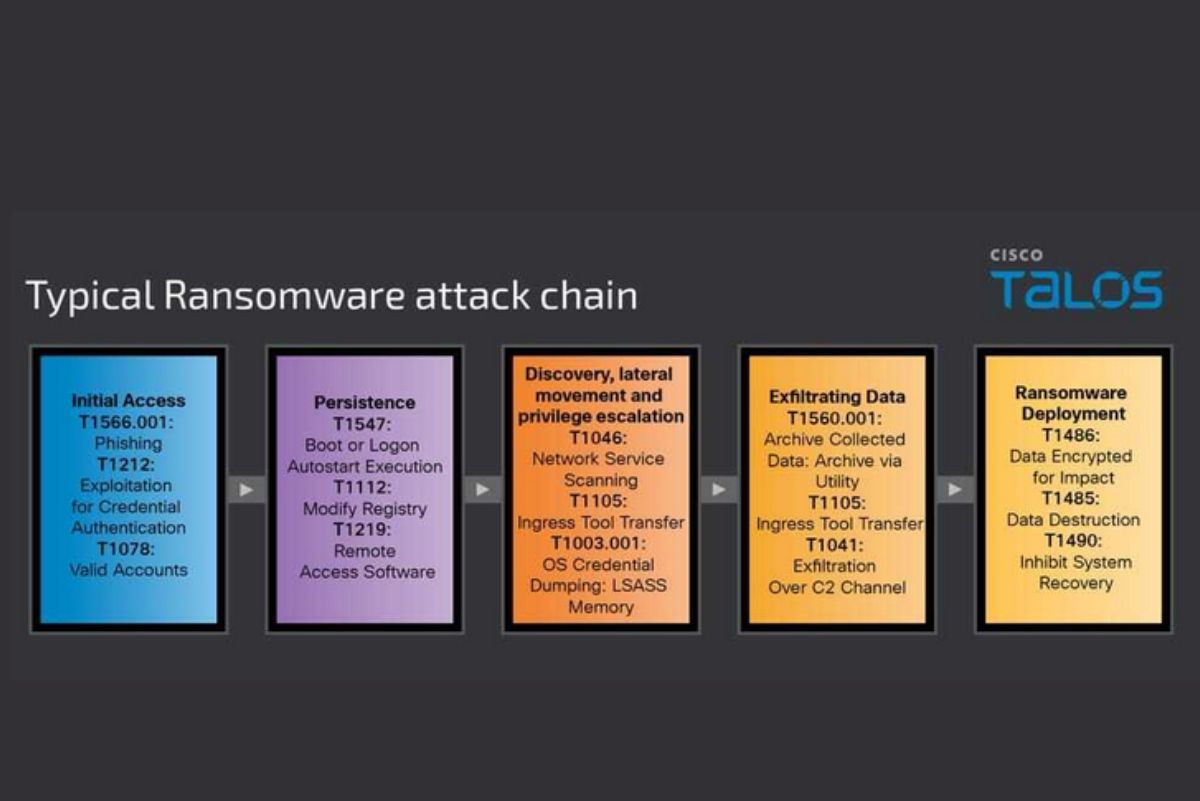
Cisco Talos Intelligence recently published a comprehensive report on the tactics, techniques, and p...

Black hat hackers have reportedly unleashed malicious software targeting over 1,500 banks and their...

According to reports from the Shadowserver Foundation, approximately 6,000 internet-accessible Palo...

Microsoft has confirmed its collaboration with CISA on an urgent directive about a cyber threat, as...

A recent report by global cybersecurity firm Sophos has highlighted the widespread exploitation of R...

A fresh wave of phishing attacks has been uncovered by cybersecurity researchers, targeting more tha...