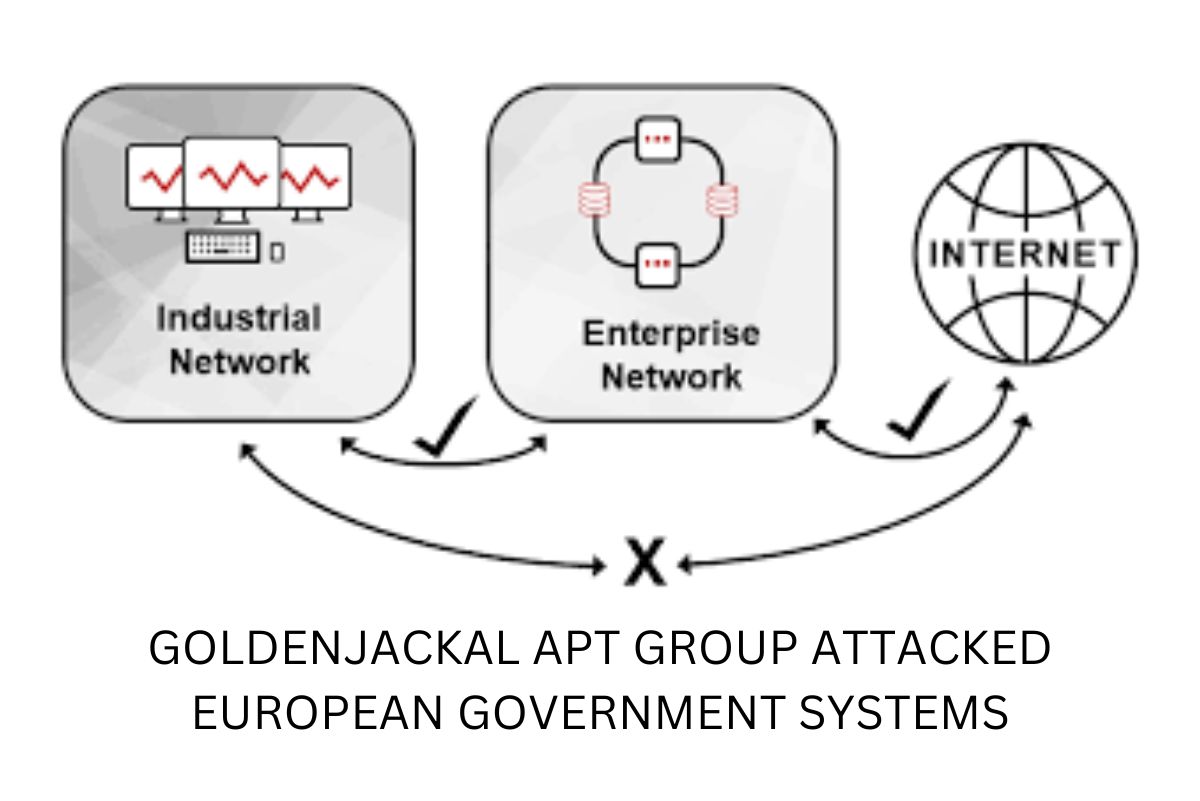
The Advanced Persistent Threat (APT) group known as GoldenJackal has successfully compromised air-gapped government systems in Europe using custom malware toolsets to steal sensitive data, including emails, encryption keys, documents, and images.
According to an ESET report, these attacks occurred on multiple occasions: once targeting the embassy of a South Asian country in Belarus in September 2019 and again in July 2021, and a more recent breach against a European government organization between May 2022 and March 2024.
In May 2023, Kaspersky highlighted GoldenJackal’s focus on government and diplomatic entities for espionage. While the group’s use of custom malware spread via USB drives, such as 'JackalWorm,' was known, successful attacks on air-gapped systems had not been confirmed until now.
GoldenJackal’s method begins by infecting internet-connected systems with a trojanized software or malicious document containing the 'GoldenDealer' malware. GoldenDealer monitors for USB drive insertions, then copies itself and additional malicious components onto the drive. When that USB drive is eventually used on an air-gapped system, the malware deploys two tools: GoldenHowl (a backdoor) and GoldenRobo (a file stealer).
GoldenRobo scans for valuable data like documents, certificates, encryption keys, and more, storing them in a hidden directory on the USB drive. Once the USB is reconnected to an internet-connected device, GoldenDealer automatically sends the stolen data to the attackers’ command and control (C2) server.
GoldenHowl, a Python-based backdoor, performs multiple functions, including file theft, persistence, vulnerability scanning, and direct communication with the C2.
Starting in 2022, GoldenJackal introduced a new modular toolset built in Go, which allowed different machines to handle distinct tasks, such as file exfiltration or configuration distribution. This new malware, named GoldenAce, continues to infect USB drives, with tools like 'GoldenUsbCopy' and its updated version 'GoldenUsbGo' stealing files based on predefined criteria.
GoldenUsbGo focuses on recently modified files (up to 14 days old), smaller than 20 MB, and containing specific content types or keywords (e.g., “password,” “login,” or “key”). It no longer uses AES-encrypted configurations, simplifying exfiltration.
Additional tools include GoldenBlacklist (or GoldenPyBlacklist), which filters and archives email messages for exfiltration, GoldenMailer for emailing stolen data, and GoldenDrive, which uploads the stolen information to Google Drive.
The presence of these overlapping toolsets, as noted by Kaspersky, demonstrates GoldenJackal’s ability to adapt and develop new malware for highly targeted espionage campaigns.
For more details on indicators of compromise (IoCs) related to these tools, check the associated GitHub page.